Time is running out for organizations and users still running Windows 7 to upgrade to Windows 10, with official support from Microsoft ending on January 14, 2020. Once Windows 7 support ends officially, the once widely used operating system will receive no updates, small or critical.
Mainstream support for Windows 7 — that is new features and usability improvements, actually ended in 2015 with the release of Windows 10, however, it still received the crucial monthly updates and critical patches that protect systems from hackers.

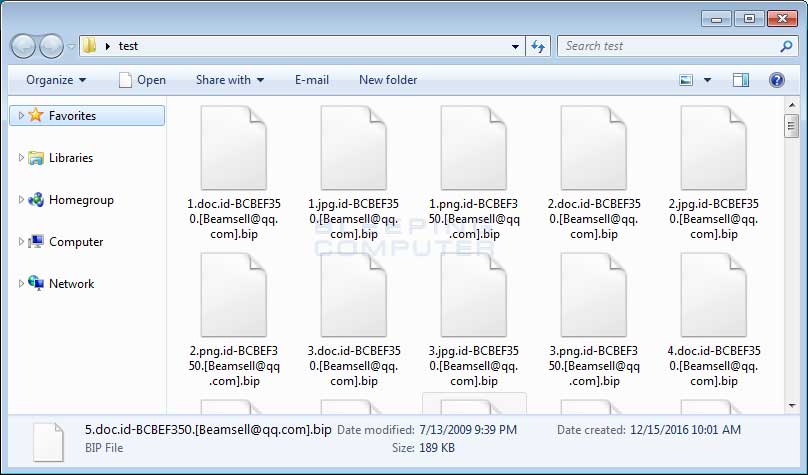
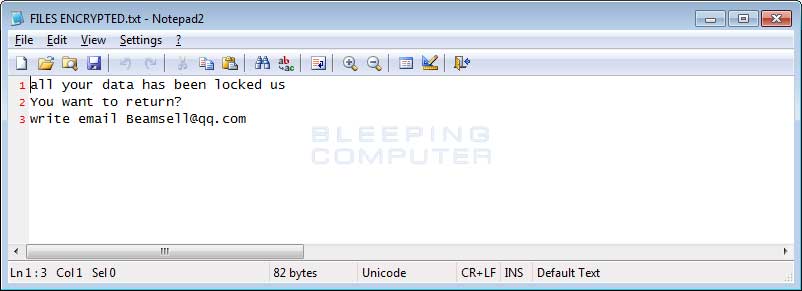
Malware is able to spread much more quickly on systems that have not received updates since hackers are able to take advantage of known compromises and spread that information to one another on the dark web and other places. The result is a messy situation in which the vulnerable systems can talk to one another to spread things like ransomware. Antivirus alone can only go so far in protecting machines that are not up to date as the backbone of the antivirus software becomes outdated as well.
“Malware is able to spread much more quickly on systems that have not received updates since hackers are able to take advantage of known compromises…”
There are still a lot of companies out there that have not completed their migration to Windows 10. In a report on TechRepublic, Sumir Karayi, founder & CEO of the security firm 1E said “There are very few companies out there that have entirely completed their Windows 10 migrations. A number have done the easy 80%—the in-place upgrades, the machine replacements—but that last 20% is proving the hardest part of the entire process.”
It is because of this that organizations have two options for retaining support past the cut-off date in 2020. An Extended Security update plan can be purchased from Microsoft directly for an undisclosed price to protect the operating system until 2023. The second option is to purchase Microsoft Virtual Desktop, a recurring subscription service from Microsoft that allows you to purchase remote access to a desktop on a server hosted in their own Azure platform for a monthly fee. These options place the support paths off the table for consumers and most small businesses, with an upgrade remaining the only feasible option.
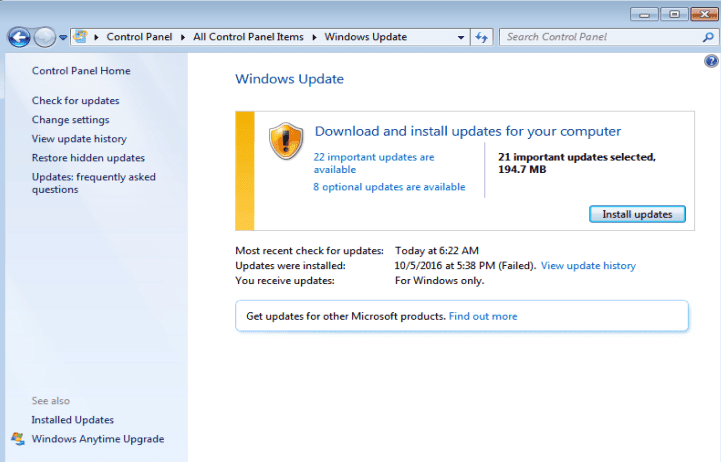
If your organization has not begun to migrate to Windows 10, there is no time to spare– you should work to have a plan in place to ensure safe operation of your network and its contained operating systems. Contact VMX Technologies today to review your network and put a plan in place if you don’t already have one. It is never too late to begin planning for tomorrow’s challenges.
Does your company have a plan for Windows 7 end-of-life? Do you intend on purchasing extended Windows 7 support from Microsoft, or migrate to another operating system entirely? Let us know below in the comments.